About ProxyDetect.live
Why ProxyDetect.live Exists
ProxyDetect.live demonstrates that modern websites and applications can reliably determine whether an incoming connection is routed through a proxy, VPN, or remote desktop solution. Years of intense marketing from anonymisation providers created the myth that VPNs are undetectable. In practice, tunnelled connections behave in a way that can be detected and the goal of this project is to proof that.
The detection engine passively inspects every connection. It correlates server-side network telemetry with optional client-side JavaScript measurements to produce a risk score in real time. No static IP blocklists are required (albeit we use some), and every visitor begins with a neutral score (no state is stored between connections).
How Proxy & VPN Detection Works
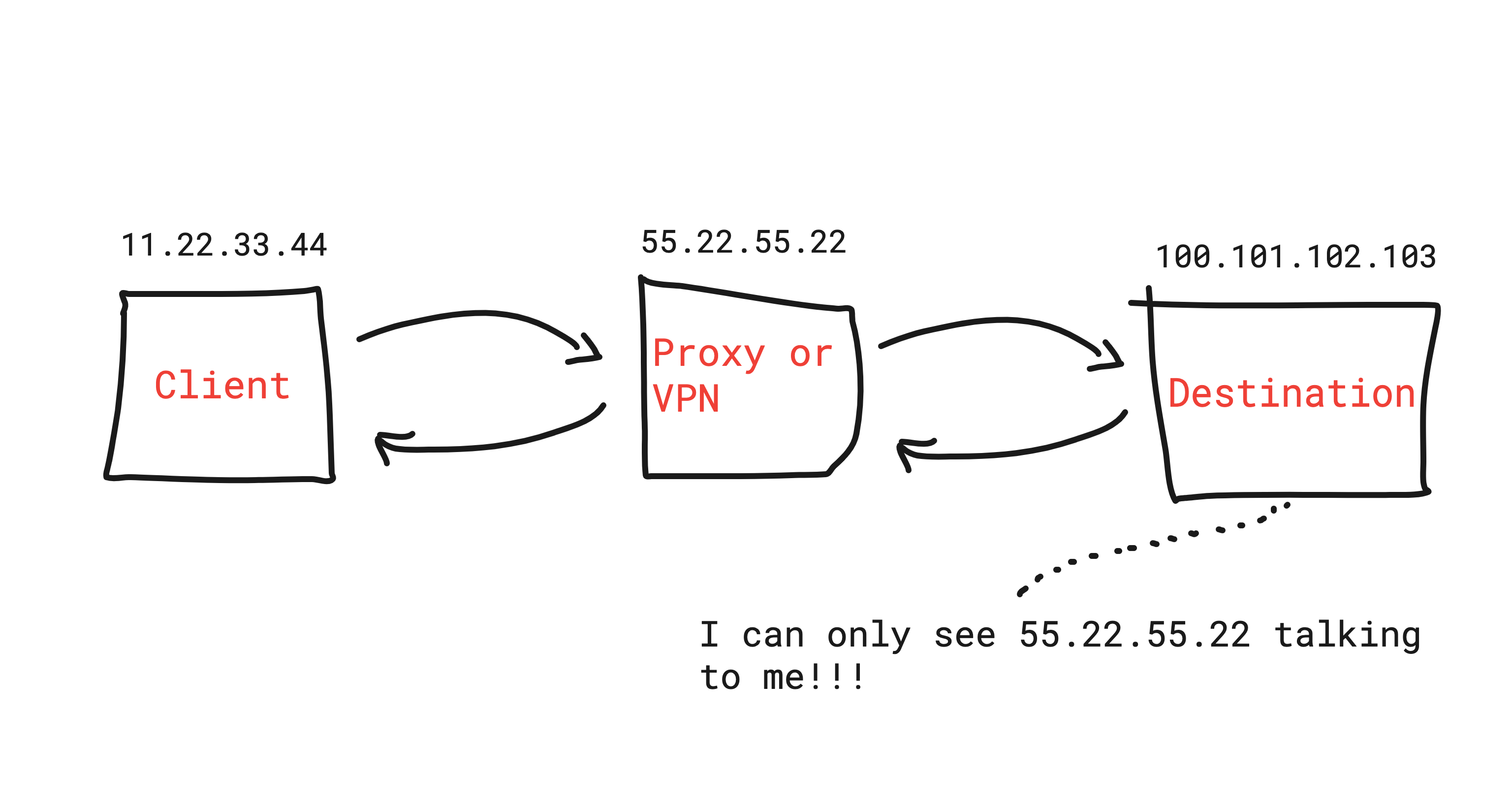
Proxies and VPNs both hide the original IP address, but they do so with different network architectures. A proxy usually operates on the transport layer, relaying specific application traffic. A VPN typically operates on the network layer, tunnelling all traffic from an interface. Because of these architectural differences, the detection strategy for each technology differs as well.
ProxyDetect.live collects passive server-side signals and, when available, client-side JavaScript telemetry. Latency data, protocol handshakes, TLS fingerprints, and DNS behaviour all contribute to the aggregated score.
Detection Accuracy
Every detection technology suffers from false positives and false negatives. ProxyDetect.live has been tuned to achieve accuracy above 95% and recall above 85% in live environments — significantly higher than traditional blocklist-based approaches.
We recommend treating the proxydetect.live score as a strong indicator rather than an absolute decision. You should combine it with follow-up challenges like SMS verification or re-authentication when you need extra assurance.
Ethical Considerations
Technology that detects tunnelled traffic can protect legitimate businesses, but it can also be misused. ProxyDetect.live is designed for risk mitigation—preventing fraud, enforcing licensing agreements, and safeguarding critical services. It is not intended to suppress free speech or endanger activists operating under oppressive regimes.
Organisations should inform users when detection is part of their security posture and comply with all relevant privacy regulations.
How Your IP Address Identifies You
On the public internet, your IP address functions as the routing identifier for your device. Internet service providers frequently map that address to verified customer information. In many countries, registering a SIM card or broadband contract requires government-issued identification. Authorities can therefore correlate a public IP with a real person or physical location when necessary.
Even where such registration is not required, investigators have alternative tools. Mobile connections can be located through GPS or cell-tower triangulation, while fixed-line providers know the exact address of their termination points.
Services such as ipapi.is illustrate how much context can be derived from an IP address: approximate location, ISP, proxy status, line type, and more.
Who Uses Proxies and VPNs?
Privacy tools are valuable to many people. Journalists, activists, and whistleblowers rely on them to avoid retaliation. However, the same tools can support large-scale fraud, credential stuffing, or content piracy (streaming services). Understanding a user's motivation helps determine the right response.
Legitimate Uses
- Journalists and activists protecting their sources and themselves from hostile regimes
- Whistleblowers and security researchers who must remain anonymous
- Individuals seeking privacy from pervasive advertising and tracking ecosystems
Legal Grey Areas
Many users install VPNs to circumvent geo-restrictions. Streaming services like the BBC iPlayer or Netflix often limit content to specific countries. VPNs can also reduce regional price discrimination on services such as Netflix or Tinder. Web scraping is another example where the legal guidance varies by jurisdiction.
Malicious and Illegal Activity
- Consuming copyrighted content without permission
- Committing cybercrime like credential-stuffing attacks or hacking
- Abusing online banking sessions to launder stolen funds
- Running spambots and large-scale phishing operations
- Operating automated scalping or sneaker bots
Proxy vs. VPN
Most anonymisation technologies fall into two broad categories: proxies and VPNs. Proxies operate on the transport layer, forwarding traffic for specific applications. VPNs typically function on the network layer, encapsulating all traffic from an interface. The diagram below shows how the two approaches map to the OSI model.
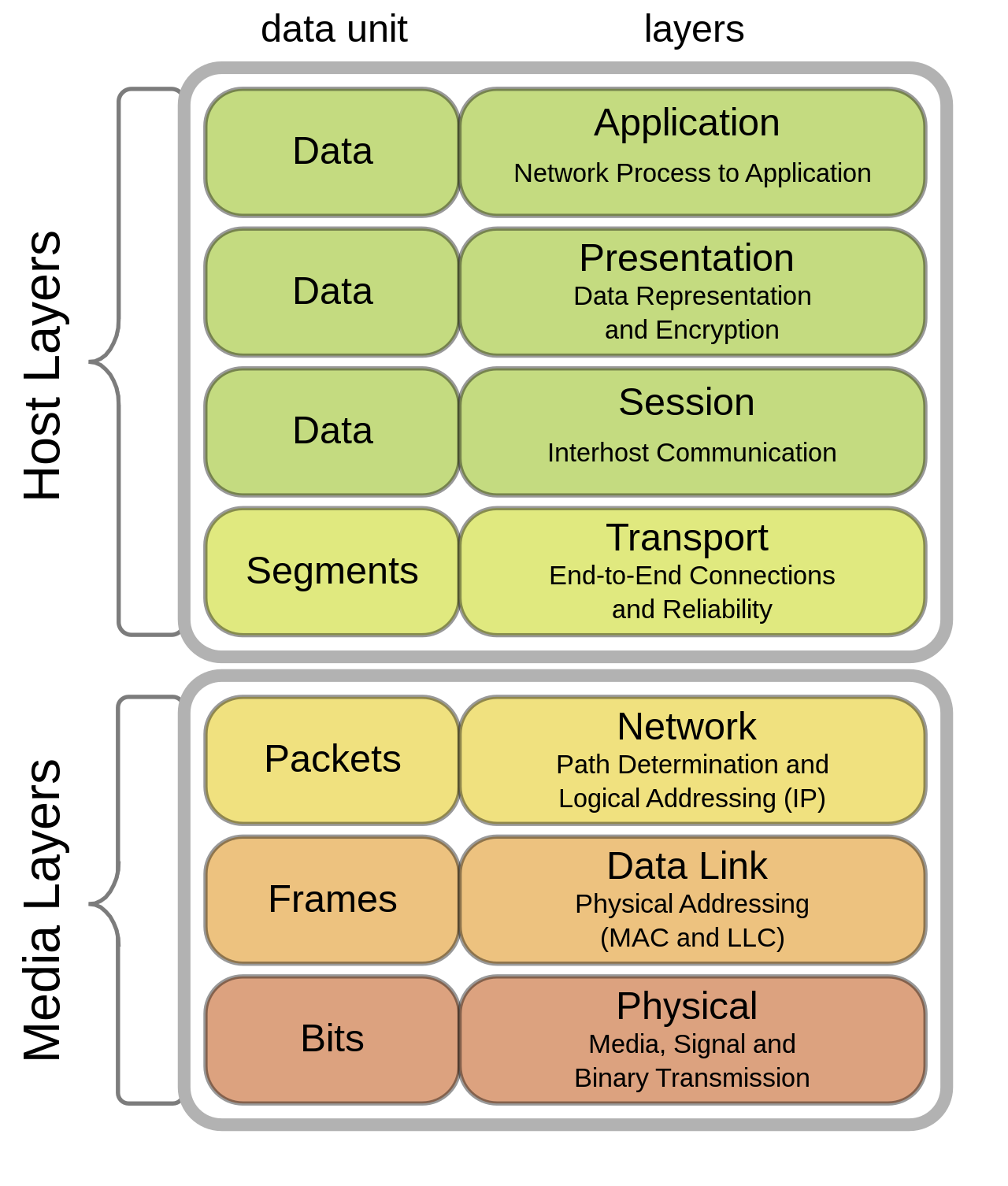
HTTP proxies use the CONNECT method to forward traffic, while SOCKS proxies implement their own protocol. The SOCKS specification is defined in RFC 1928; HTTP proxy behaviour is documented in RFC 2068.
Detection Model
The detection workflow is straightforward: a user visits proxydetect.live with a modern browser. The site collects sandboxed JavaScript signals, while the server runs passive analysis on the incoming connection. The combined evidence determines whether the session is likely routed through a proxy or VPN.
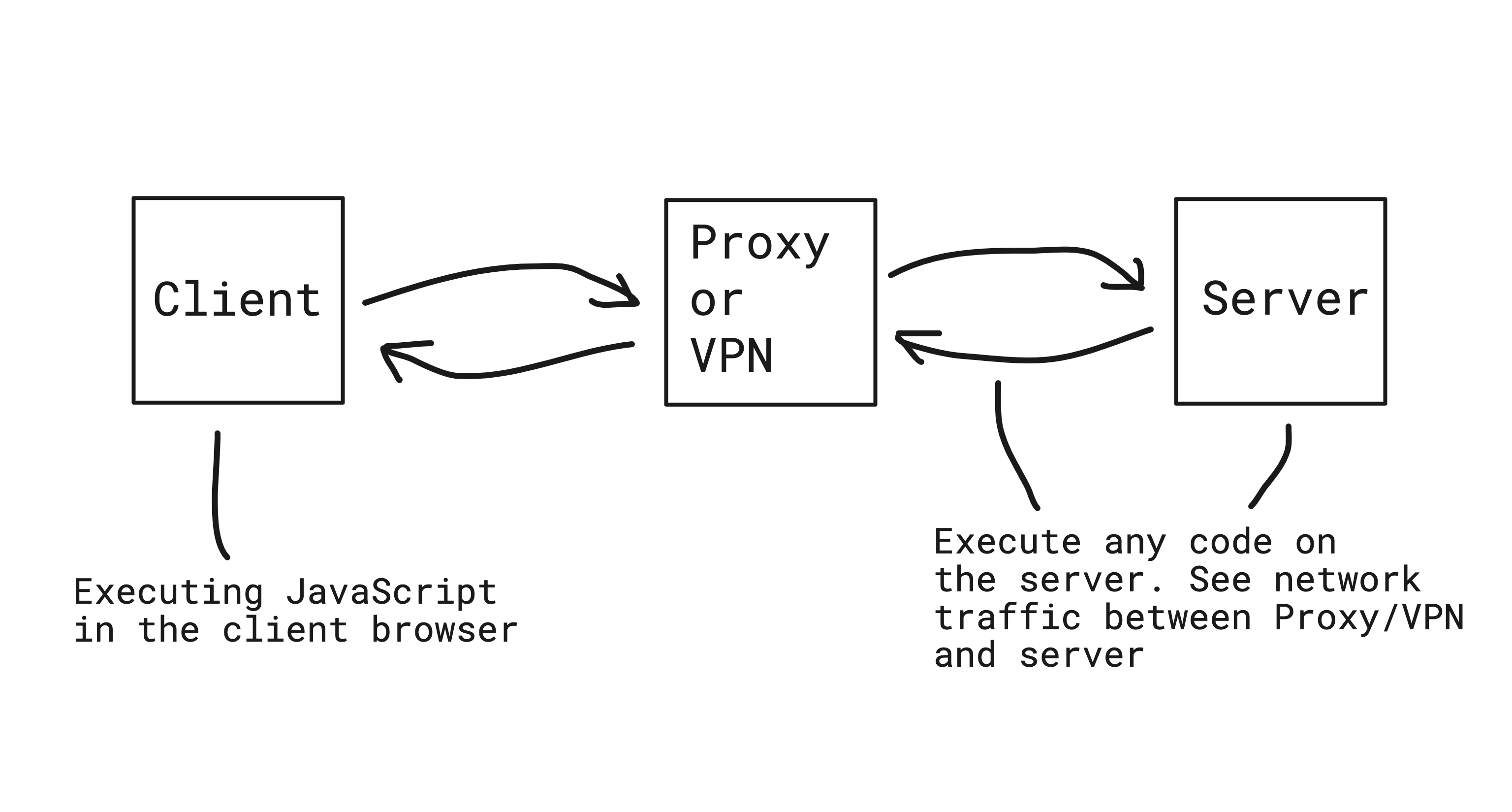
Detection is challenging because browsers run in a restricted sandbox, and only limited client-side information is available without elevated permissions. ProxyDetect.live therefore leans heavily on network behaviour and passive signals. After all, detection should also work even if the user disables JavaScript.
Software & Protocols
VPN Software Examples
VPN protocols define how packets are encrypted, authenticated, and routed through the tunnel. While TCP is possible, most modern VPNs prefer UDP for performance reasons. Widely deployed VPN technologies include:
- IKEv2 – Popular on mobile devices thanks to seamless roaming between Wi-Fi and cellular networks.
- WireGuard® – A modern, lean VPN protocol focused on speed and simplicity while using state-of-the-art cryptography.
- OpenVPN – The most recognized VPN implementation, capable of operating over UDP or TCP with the OpenSSL library.
- PPTP – An obsolete protocol; numerous security issues make it unsuitable today.
- SSTP – Secure Socket Tunneling Protocol encapsulates PPP traffic inside TLS, providing built-in encryption and integrity checks.
Proxy Software Examples
Proxy infrastructures often rely on either HTTP or SOCKS. Popular open-source implementations include:
- Squid – A caching proxy that supports HTTP, HTTPS, FTP, and more, frequently used to accelerate web traffic.
- Dante – A full-featured SOCKS server and client that implements RFC 1928 and related standards.
- 3Proxy – A lightweight, cross-platform proxy suite supporting HTTP, HTTPS, SOCKS, POP3, SMTP, and more.
- GoProxy – A high-performance proxy written in Go that supports HTTP, HTTPS, SOCKS5, TCP, and UDP relays.
- simple-socks – A minimal SOCKS5 server for Node.js, useful for testing and experimentation.
Commercial Providers
VPN Providers
VPN services are plentiful because it is easy to rent cloud infrastructure and deploy a VPN endpoint. Some of the most recognisable names are:
- NordVPN – Offers secure, encrypted tunnels and additional features such as Meshnet and dedicated IPs.
- ExpressVPN – Provides reliable performance across 94 countries with proprietary Lightway protocol support.
- Surfshark – Known for unlimited device connections and network obfuscation features.
- Private Internet Access – Focuses on privacy and open-source software with a large US presence.
- Proton VPN – Emphasizes transparency, strong privacy policies, and advanced Secure Core routing.
Proxy Providers
Proxy providers specialise in residential, mobile, or datacentre IP pools. Well-known examples include:
- Bright Data – Offers extensive proxy networks, web scrapers, and prebuilt datasets.
- Oxylabs – Supplies datacentre, residential, and mobile proxies with scraper APIs.
- IPRoyal – Provides a large global proxy network with ethically sourced IP addresses.
- Smartproxy – Focuses on easy-to-use proxy access for sales intelligence and data gathering.
- Airproxy – Delivers dedicated mobile proxies with carrier-grade routing.
- Proxidize – Provides hardware and software to build custom mobile proxy networks.